On Friday morning (February 17), I received a nonconsensual installation of 180solutions Zango software through a security exploit. I was browsing an ordinary commercial web site, when I got a popup from exitexchange.com (a major US ad network, with headquarters in Portland, Oregon) . The popup sent me to a third-party’s web site. (I’ll call that third party “X” for convenience. Details.) Then X ran a series of exploits to take control of my test PC, including using the widely-reported WMF exploit uncovered last month. Once X took control of my PC, X caused my computer to install and run 180solutions Zango software, among a dozen other programs. Notably, X fully installed 180’s Zango without me taking any action whatsoever — without me clicking “I agree,” “Yes,” “Finish,” or any other button of any kind. X installed 180’s Zango despite 180’s new “S3” protections, intended to block these nonconsensual installations.
Most aspects of this installation are remarkably standard. “Adware” installations through security exploits are all too common. And it’s not that unusual to see traffic flowing through an ad network — even a big US ad network.
But what’s newsworthy here is that 180solutions got installed, even though 180 last year told the world that these nonconsensual installations were impossible. Effective January 1, 2006, all 180solutions distributors were required to switch to 180’s “S3” installer. 180 claimed huge benefits from the new S3 system: 180’s October 2005 press release promised:
“The S3-enabled clients … mean[] 180solutions will own the entire experience from beginning to end on all installations of its products.”
180’s S3 Whitepaper (PDF) also falsely promises major benefits from S3:
“[I]nstallation cannot continue until the user gives consent.”
“Since the consent box comes directly from 180solutions, publishers are unable to turn it off.”
To the contrary, my video shows installation continuing even when a user does not consent. And my video shows a distributor faking a user’s click on the consent button.
See video of the nonconsensual installation of 180 Zango, including bypassing of the 180 S3 screen. (Note: Video has been edited to hide the identity of the installer at issue. Learn why. Within the video, yellow markup provides my comments and analysis.)
180’s S3 Technology and Its Design Flaws
Historically, 180’s installer programs have installed 180 software immediately, on the misguided assumption that 180’s distributors already obtained user consent. That approach is overly optimistic because 180’s distributors have no incentive to ask users’ permission: If distributors seek users’ permission, users might decline that unwanted offer, preventing distributors from getting paid by 180. So it comes as no surprise that many distributors have installed 180 without obtaining users’ consent. I have publicly posted at least five different videos showing such installations (1, 2, 3, 4, 5), and I have many more on file. Others have repeatedly found the same (1, 2, 3, 4, 5).
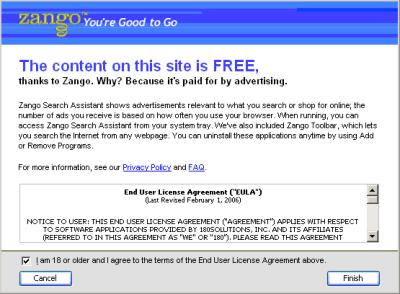
180’s S3 system seeks to address these nonconsensual installations by showing users a notice screen before 180solutions software installs onto their PCs. 180’s distributors are now supposed to run 180’s “stub” installer to display this notice screen; then users can choose whether or not to proceed. See example screen at right.
As a threshold matter, I don’t think 180’s S3 screen provides an accurate, truthful, complete disclosure of 180’s important effects. As I explained last month, the S3 screen oddly describes 180 only as showing “ads,” without mentioning that these ads appear in “pop-ups” — the essential characteristic reasonable users most need to know in order to decide whether they want 180’s software. The S3 screen also fails to describe the important privacy effects of installing 180’s software — that 180’s software will tell 180’s servers many of the sites users visit. The S3 screen does show a EULA — but it’s in an oddly-shaped box, and its text can’t be copied to the clipboard. Finally, the S3 screen labels its affirmative button “Finish” — even though the S3 screen is known to appear in circumstances where it is the first screen mentioning installation of 180’s software. A user cannot be asked to “finish” what he has not yet agreed to start; an “I agree” or “I accept” label would more clearly indicating the consent that the button is claimed to grant.
But beyond these important problems of wording and layout, the S3 installer also features a fundamental design flaw: Self-interested installers can easily bypass the S3 prompt. Installers can easily fake a click on the “Finish” button — just by simulating a single stroke of the “enter” key, or by simulating a click on a predictable button location. So faking a user’s consent is trivial — just a single Windows SendKeys API call.
Sure enough, my “X” installation reflects an installer using exactly these methods. In my video of X’s exploit-based installation of 180, the S3 notice was visible on screen for less than half a second — between 19.08 seconds and 19.57 seconds into the video. During that half-second, exploit-delivered software (installed on my test PC mere seconds before) pressed “Finish,” at which point 180 completed its installation, putting itself in my System Tray (next to the Windows clock), beginning to download its supplemental files, and beginning to monitor my web browsing.
180’s Bad Partners and 180’s Flawed Business Model
180 seems to intend its S3 installer to protect 180 and users from the untrustworthiness of 180’s distribution partners. 180 is right to think that S3 makes it somewhat harder for distributors to install 180 without getting users’ consent. But the increase in difficulty isn’t much — certainly not enough to deter any serious installer. Those who want to get paid for installing 180 will find that S3 presents at most a small speedbump; it’s hardly the airtight blockade 180’s press release claims.
For 180, the appropriate response to nonconsensual installations is not merely a small improvement in installer program design. Rather, 180 should rethink its entire distribution business model. 180 has repeatedly written about the “long tail” of distributors (1, 2, 3) — 180’s plan for thousands of different web sites installing 180’s software when users browse their materials, and thousands of different programs bundling 180. It’s an interesting vision, but in my view impractical and unwise. With so many distributors, 180 will be unable to assure that each distributor really does obtain consent — rather than cheating the system, as X did.
180’s October press release correctly describes the serious harms that occur when users receive many advertising programs. “A myriad of unwanted software … can often negatively impact system performance,” 180 admitted. But 180 then claimed that S3 would keep 180 out of such bundles. I disagree. According to my records, the installation at issue also installed Ad-w-a-r-e, Adservs, Integrated Search Technologies, Internet Optimizer, Media Tickets, New.net, Quicklinks, Surfsidekick, Tagasaurus, Targetsaver, Toolbar888, Ucmore, Webhancer, Web Nexus, WinFixer, and more. These many programs collectively bombarded my test PC with an incredible 730 registry keys, 1194 registry values, 461 files, and 43 file folders. Worse, the newly-installed programs caused 61 processes to run on my test PC, via 24 EXEs set to load each time I turned on my computer. The programs even added three different toolbars to my web browser. This overwhelming burden made it difficult even to inventory and track the programs’ additions and effects. So many co-bundled programs hardly satisfy the “prevent[ing] customers … from receiving a myriad of unwanted software” promise in 180’s press release.
Why “X” and an Obscured Video?
Long-time visitors to my web site may reasonably wonder: Why the markings in my screen-capture video? And why refer to the 180 distributor as “X,” rather than by its actual name and URL? After all, I’ve long provided video proof of my observations, and I’ve been naming names ever since my 2003 listing of advertisers using Gator (now Claria).
But I’ve run out of patience for being outside quality control staff for 180solutions. An episode last month was particularly instructive: Security company FaceTime found an AOL Instant Messenger worm that was installing 180solutions. 180’s response? After FaceTime reported the details, 180 trivialized the finding and issued a self-serving press release. Rather than admit that their software still becomes installed improperly, 180 danced around the issue and tried to use these wrongful installations to obtain a public relations benefit.
CDT‘s experience with 180 is similarly instructive. After two years of alerting 180solutions to its various bad practices, CDT recently ceased working with 180, instead electing to file a complaint with the FTC.
I too have decided no longer to share my work with 180solutions. As discussed in the preceding section, I have concluded that 180’s business model is fundamentally broken — that 180 cannot implement technology or enforcement to assure the proper installation of its software. Accordingly, just as CDT terminated its discussions with 180, I have resolved not to tell 180solutions which specific distributor was responsible for this installation.
Despite my decision not to work with 180 on resolving these installations, I will make my research available to those with a legitimate need to know. I expect to provide (and in some cases already have provided) this information to law enforcement officials considering action against 180solutions, to private attorneys in litigation against 180solutions, to members of the press seeking to verify my findings, and to other security researchers. Please contact me to request the original raw video file. As usual, I also retain full packet logs, raw screen-captures, registry change logs, filesystem change logs, HijackThis logs, Ad-Aware logs, and additional records.
Update (February 24): My Response to 180’s Press Release
180solutions has found and terminated the distributor I described above, which I’m now happy to reveal was crosskirknet.com. But what a road to get there! 180’s press release suggests 180 figured this all out within hours of my initial post. I’m convinced that that’s false. First, 180 terminated some other bad installer — only later realizing that the installer I found was someone different. Sunbelt has the details — how we figured out (and proved) that 180 hadn’t cut off this installer when 180 issued the press release saying they had. In a blog post, 180 now admits that we’re right and their press release was wrong. (Of course the right response to a false statement in a press release is a correction press release, not a mere blog post. Otherwise, many readers might get the press release, e.g. via the news wire, but never see the blog post.).
180’s press release claims that S3 “enabled the company to go back and re-message every user who received its software [from this nonconsensual installer] and provide them a one-click uninstall.” 180’s blog says the same: “We re-messaged each of [these] installs and provided … a one-click uninstall of our software.” In both documents, 180 writes in the past tense (“enabled”, “re-messaged”, “provided” ), seemingly indicating that these re-notifications have already occurred. But I have yet to receive any such prompt, despite substantial efforts to seek it out (e.g. by repeatedly restarting my test PC). I’ve also received many 180solutions ads on my infected test PC, despite 180’s claim that it “shut off all advertisements to all installs” from this distributor. So here too, I think 180’s statements are off-base. 180 may intend or aspire to provide renotifications, and 180 may intend to shut off ads. But by all indications, 180 hasn’t actually done so, at least not yet. I’ve confirmed my findings with Sunbelt; they haven’t seen this re-notification either, and they’re still getting ads too.
180’s press release quotes 180’s CEO as saying “No software is ever hack-proof.” I agree. But 180 has previously made public statements falsely indicating that its software is not susceptible to those who want to install 180 without consent. Recall 180’s S3 Whitepaper (PDF), explicitly stating “[I]nstallation cannot continue until the user gives consent” and “Publishers are unable to turn [the consent screen] off” (emphasis added). These are not claims of mere hopes or aspirations. No, 180 promised that installation “cannot” proceed without consent. But now that I’ve disproven 180’s claim, 180 tries to backpeddle and to weaken its unambiguous statement. The better approach would be to admit that 180’s prior promises went too far, and that 180’s software cannot actually deliver the benefits 180 previously described.
180’s press release concludes with a section 180 labels “a call for ‘responsible disclosure’.” Citing practice among those who find security vulnerabilities in widely-deployed software, 180 says researchers should tell 180 when they find nonconsensual installations of its software, rather than keep this information to themselves or provide it to law enforcement. I understand that 180 would like to receive this information, and I do follow responsible disclosure principles when I find software vulnerabilities. But responsible disclosure principles just don’t apply to records of nonconsensual installations.
Responsible disclosure principles seek to prevent hackers from taking advantage of newly-uncovered security vulnerabilities. If hackers learned about vulnerabilities before software vendors had time to prepare patches, users would face increased security risks, with few good options for protection. So responsible disclosure principles have a clear purpose and a clear benefit to users — which is why I followed these principles when I previously found vulnerabilities in widely-deployed software.
But what I uncovered, above, is not a security vulnerability. I didn’t find a new security hole, or a new way to take advantage of some existing hole. All I found was some bad guy who’s already using these methods — and who 180 has been prepared to pay for his efforts. There’s no heightened risk of harm to users from my reporting what’s already happening. Perhaps this particular bad actor got to continue his scheme for a few more days while 180 struggled to figure out who was responsible. But that’s the entire harm that resulted from my refusal to tell 180 what happened — that’s the usual, background, ongoing risk of harm; it’s not a heightened risk created by my disclosure itself. When I posted information about these nonconsensual 180 installs, I didn’t put users at special risk of any worm or exploit, in the way that responsible disclosure principles intend to prevent.
So where does this leave us? 180’s S3 system is still broken in all the ways I initially set out. 180’s press release made claims that can be shown to be false, as did 180’s prior statements of S3’s benefits, but 180 has not properly retracted its false statements. And 180’s analogies don’t add up. I’d still like to see 180 spend more time improving its practices, and less time on premature press releases and public relations.
Thanks to TechSmith for providing me with a complimentary license of its Camtasia Studio, the video annotation software I used to mark up my screen-capture video of this installation.